
Security is getting a lot of attention. A lot of environments have heard of security but have applied it into their IT in a very limited way. I have worked at and seen organizations grow from being a totally hacked places into a "reasonably" secure environments. Its not just the security its also the policy. Policy makers and enforcers in the legacy IT infrastructure have found ways to do things in the typical DMZ/Secure infrastructures.
Although I do notice a considerable shift from the DMZ/Secure into more of a "Application Pooling" the security still remains in the same place. The pix needs to be configured but cannot enforce a typical fine-grained IPS/IDS from its end. I am not saying that its impossible but I see a severe need to do it in a more "Per Application Pool" basis.
But how are you going to enforce and even manage the great new way of provisioning a fully tested and patched "Appliance" from environment to environment? Virtualization makes all of things possible due to its flexibility. Today I have the flexibility to provision and patch a single development server for a contracted developer myself. But imagine if you have to have that whole suite of applications that need to be patched, conforming to the ITIL that an organization may have in place, move it from development to test to staging to production? And they go about it and do the patching in the production. So all I am saying is that the flexibility and enhanced productivity comes at a cost. Your security policy has to be really rock hard and tested before you begin buying all kinds of pormises and tools and finally cannot find an adequate fit within the exisiting (physical infrastructure) and the new (Virtual Infrastructure). Business has to go on and end users do not have to notice the change from physical to virtual and in production the changes through breakthrough technologies like VMotion (from VMware). Security may sound like a hype to many but since Virtualization is becoming a serious business, its time for serious actions.
An excerpt from the White Paper: (Virtual Shield data sheet will be released on monday):
In today’s data center, most of the security is provided by special purpose appliances. Contrary to the general trend of virtualization, these appliances are all-too-tangible. If a data center manager was to arrange all the servers in a big pool, the security devices would, by necessity, form a static ring around the
pool. Segmentation of some sort is necessary, since the server pool may contain servers of different “tiers” of criticality (for example, Web servers facing the public and databases containing sensitive data). The servers need to be protected from the outside world, but they also need to be protected from each other. If a single server in the pool is infected with a rapidly propagating threat then it will be able to cross-infect all other servers that contain the same exposed vulnerability.
Up to now, data center, security and network architects have had to reach a compromise of sorts – servers are on separate virtual networks (VLANs), which are switched through firewalls sitting in a ring around the server pool. Effectively, we end up using network virtualization to compensate for the lack of
security virtualization. This approach is far from ideal, however. Since the security devices are static, they cannot respond to changes in the virtual servers. Let’s say for example that a virtual server has to be moved to another physical server for maintenance. The security associations have to follow that server, so
in order to keep things working, the server must retain the same IP address and VLAN as before.
Because of limited orchestration between the virtual servers and the non-virtual security, everything has to be done with VLANs. The disadvantage is that VLANs are difficult to manage and they are too coarse-grained for use as security controls. If you bunch all databases together you end up with the risk of cross-contamination. If you split each server into a separate VLAN you run out of VLANs. And in either
case you have a management mess on your hands.
Excellent paper and an eye opener. Thanks to Blue Lane VP for letting me peek through their Virtual Shield as well. Watch out for the paper on monday. This ought to come out by monday. Do check out some self-explanatory screenshots:
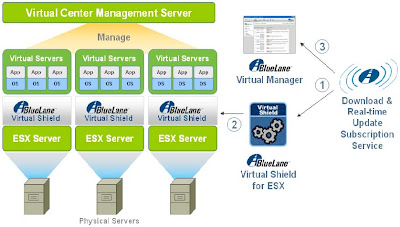
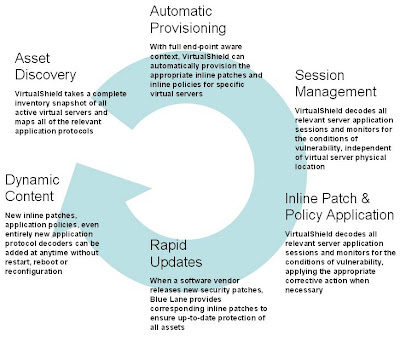
Virtual Shield Manager
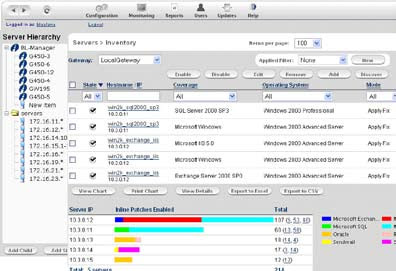
In the meantime get this copy here.
Comments
Post a Comment